You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
xF2 Add-on [DigitalPoint] Security & Passkeys 1.1.8
No permission to download
- Author SNap!
- Creation date
If you use the Days to auto-extend two-step device trust setting, the addon will always set the tfa_trust cookie when the user_remember record is extended (since we can't see the cookie duration on the server-side). Before we were only setting the cookie if the user_tfa_trusted.trusted_until value changed.
This will make it work as expected even if you had something unrelated (like a different addon) altering the user_tfa_trusted.trusted_until value (where you had a short cookie duration, but a long user_tfa_trusted.trusted_until value).
If you aren't using XenForo 2.3, you don't need to upgrade (might be some unmeasurable speed increase [think nanoseconds] when running its JavaScript since it doesn't dip into jQuery any longer).
- Entropy for challenge changed from 192-bits to 768-bits
- All JavaScript has been rewritten to be "native" (does not use jQuery) in preparation for removal of jQuery in XenForo 2.3.
I think this may have been the cause for a couple cases where an invalid Passkey record was saved to a user account. Previously, if an exception happened, it blindly accepted the null Passkey record as the new Passkey. If things went as expected (most cases) it wouldn't matter, but not everything always goes as expected.
- Added dataList-row--noHover class so background color doesn't change when the mouse moves over the table of two-step options a user has
- If an exception happens when Passkey is added to user account, present the user with an error that the Passkey could not be registered and log the underlying exception message to the XenForo error log (and most importantly, don't save an invalid Passkey registration as a new Passkey)
Added additional sanity check to ensure the device trust record is valid and exists before trying to extend it.
Fixes an issue where certain (most) security keys couldn't properly authenticate as a two-step verification option.
- Added ability to view and delete remembered sessions in admin area (new Sessions tab when editing a user)
- Fix for PHP warning when on PHP 8 and accessing site through localhost (a test setup)
This doesn't change anything for users that already have it installed. The net change is now you can use it with PHP 7.1+ (the previous requirements were PHP 7.3+).
- Checking for PHP version 7.1.0 or higher
- Removed dependency on third-party library to get list of countries for sessions and trusted devices
This doesn't change anything for users that already have it installed. The net change is now you can use it with PHP 7.1+ (the previous requirements were PHP 7.3+).
- Checking for PHP version 7.1.0 or higher
- Removed dependency on third-party library to get list of countries for sessions and trusted devices
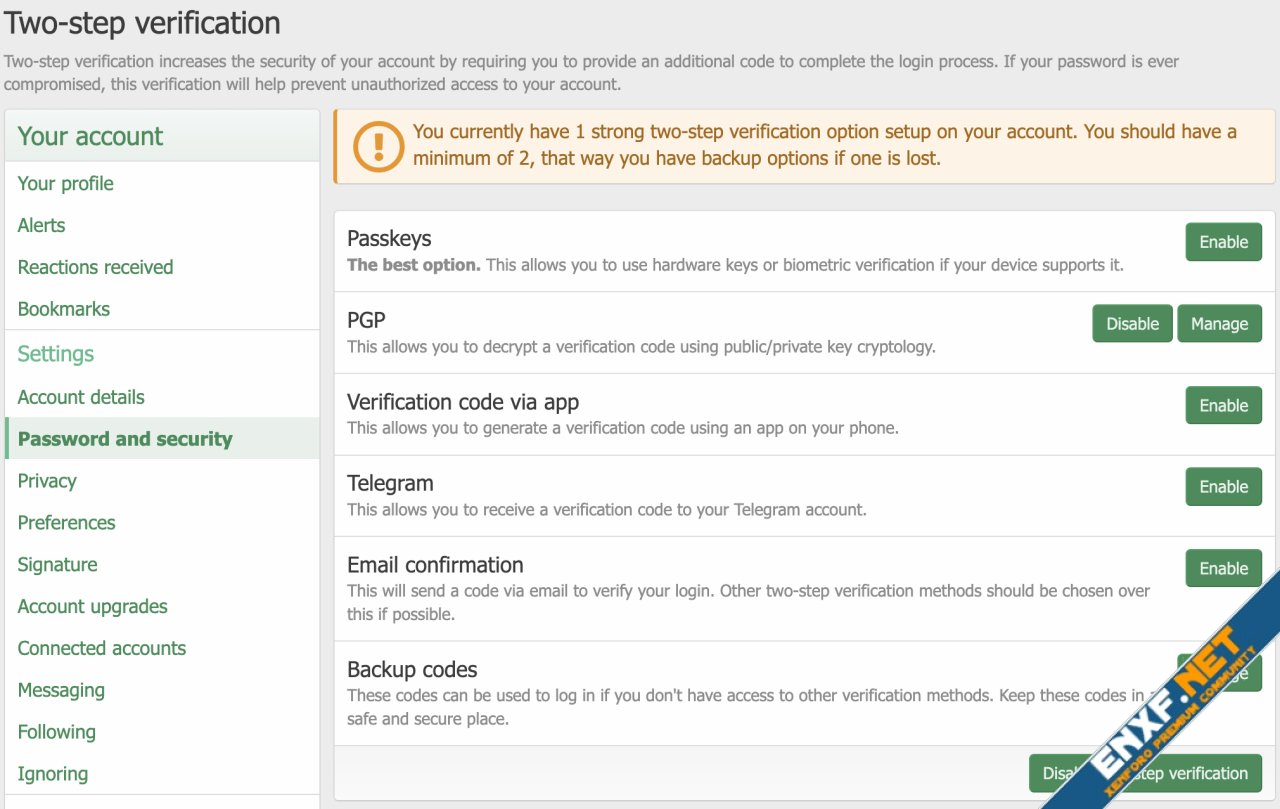
If a user doesn't have the minimum recommended strong two-step options setup on their account, their two-step page will have a notice at the top like so:
- If user has no Passkeys setup yet, the button to manage them is labeled 'Enable' rather than 'Manage'
- Use a more specific selector when enabling/disabling the Submit button on the WebAuthn form
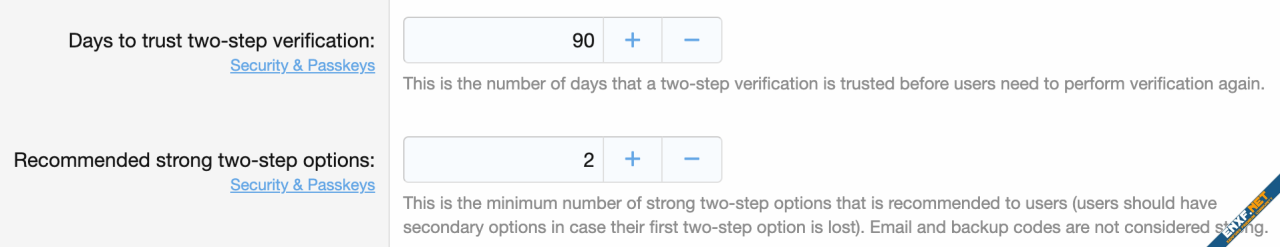
- New option: Options -> User options -> Recommended strong two-step options (defaults to 2)
- The user's two-step page will show a notice about not having enough strong two-step options if they have less than the number set under options (a reminder to users that they should have more than one good two-step options in case they lose access to one)
You can set what you want that minimum to be under user options: